
Here is a great infographic from YunYun Chen from ConsenSys originally published at: https://media.consensys.net/ever-wonder-how-merkle-trees-work-c2f8b7100ed3
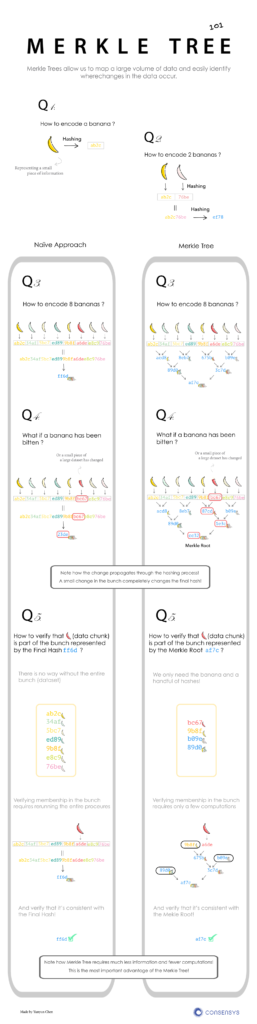
Here is a link to a 10 page research paper called “A digital signature based on conventional encryption function” by Ralph C. Merkle in 1988.
https://people.eecs.berkeley.edu/~raluca/cs261-f15/readings/merkle.pdf
This is a 7 page paper on “Providing Authentication and Integrity in Outsourced Databases using Merkle Hash Tree’s”
https://people.eecs.berkeley.edu/~raluca/cs261-f15/readings/merkleodb.pdf
